Cloud security is currently top of mind for IT.
In this post, I’ll provide a 10-point checklist to help you secure your OpenStack Neutron networking service. For starters, ensure that you use “defense in depth” as the primary security strategy and deploy a series of defensive mechanisms, as no single method exists for successfully protecting your entire service. This strategy ensures that even if one mechanism is compromised, another will be there to defend against the attack. Design network security in layers. So, instead of creating a single layer of network security protection at the perimeter, apply network security to every layer of the network, every component of the networking service and the communication channel
Here’s the security checklist. Do keep in mind that this is not a complete list of every possible defensive mechanism that you could employ. The purpose is to provide some key security checks that you could use.
- Are all interactions with the networking service isolated into security domains with proper network segmentation?
- Does your ML2 mechanism driver mitigate ARP spoofing?
- Have you considered the pros and cons of supporting various tenant network types such as Flat, VLAN, VXLAN etc.?
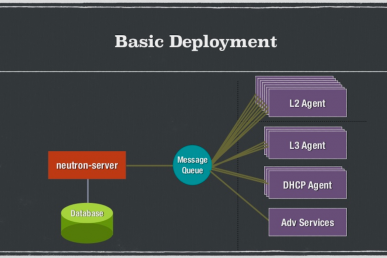
- Have you hardened the Host OS, vSwitch, Message Queue and SQL Database?
- Have you patched all reported Neutron security vulnerabilities?
- Are you using neutron security-groups and enabled port-security?
- Are all communications using SSL encryption?
- Has API access been secured using role-based access control (RBAC) by using the concept of least privilege?
- Have you investigated the maturity and security features of the various pluggable neutron components used?
- Are you using quotas to limit project resources?
- Demystifying Confidential Containers with a Live Kata Containers Demo - July 13, 2023
- OpenInfra Summit Vancouver Recap: 50 things You Need to Know - June 16, 2023
- Congratulations to the 2023 Superuser Awards Winner: Bloomberg - June 13, 2023
For more in-depth information, check out my 38-minute talk on this topic at recent Boston OpenStack Summit.
I value your feedback. Feel free to comment and share your thoughts on this topic.
Naveen Joy, who calls himself a “Neutron hacker,” is also technical leader at Cisco Systems in the chief technology and architecture office. This post first appeared on Cisco’s Cloud Blog.
Superuser is always interested in community content, contact editorATsuperuser.org.

)